Obfuscation experiment for some cryptominers.
The cryptominer
We used the Wasm cryptominer from bitcoinpeople.online.wasm and subjected it to wasm-mutate for a duration of 1 hour, resulting in 18,877 variations from the original program. The mutation process is wholly random. Given that each newly generated variant serves as the seed for the subsequent one, wasm-mutate progressively mutates the original cryptominer. After each binary is generated, we construct a square image, translating each byte in the binary into a grayscale value ranging from 0 to 255. Let’s examine the outcome.




Another target
We did the same for a Wasm binary that we knew was not a crypto miner. Check the results.
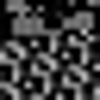



Some preliminary conclusions
Denoising
Adhering to the algorithm suggested in the MINOS study [?], we “reshaped” all images into 100x100 square pictures. This action represents the initial step in transforming Wasm binaries into images. We streamlined the succeeding steps of MINOS to enable a preliminary and manual evaluation of our obfuscation method.
We have noticed two phenomena. Firstly, following multiple iterations, the images derived from wasm-mutate variants begin to converge pixel values, implying that during the image conversion process, a cluster of pixels gets approximated to a single color value. This suggests that any two Wasm files, whether crypto-related or not, could be convoluted into the same image.
Secondly, we created two variant populations for two distinct binaries. Within these populations, we discovered pairs of variants (with one variant from the cryptominer and another from a non-crypto program) that closely resembled each other in terms of their imaging. This suggests that our method can effectively fool the human eye. We are presently replicating the classifier’s implementation to verify if wasm-mutate can indeed generate malware undetected by contemporary defenses.
Our final conjecture is that malware classifiers based on the “imaging” of Wasm binaries can be circumvented with the appropriate obfuscation process.